Cybersecurity in Higher Education: Problems and Solutions
Cybersecurity challenges abound in higher education. This article explores the cybersecurity threats that the higher education space faces, as well as a range of solutions that can help colleges and universities combat future attacks.
Institutions of higher learning face a constant deluge of cyberattacks. Following an incident in 2015, Kevin Morooney – former Vice Provost for Information Technology at Pennsylvania State University – told The New York Times that Penn State faced an average of 20 million attacks per day, an amount “typical for a research university.”
Beginning with a small sample of the financial effects that such threats can have, digital forensics and cybersecurity firm LIFARS estimated in a 2016 report that Spear Phishing attacks – designed to infiltrate an organization and steal sensitive information, often via email – cost businesses an average of $1.8 million per incident. In a 2017 report, Cybersecurity Ventures predicted that attacks involving Ransomware – which threaten to steal, block or publish a victim’s data unless a ransom is paid – would cause roughly $5 billion in damages in 2017, up from $325 million in 2015.
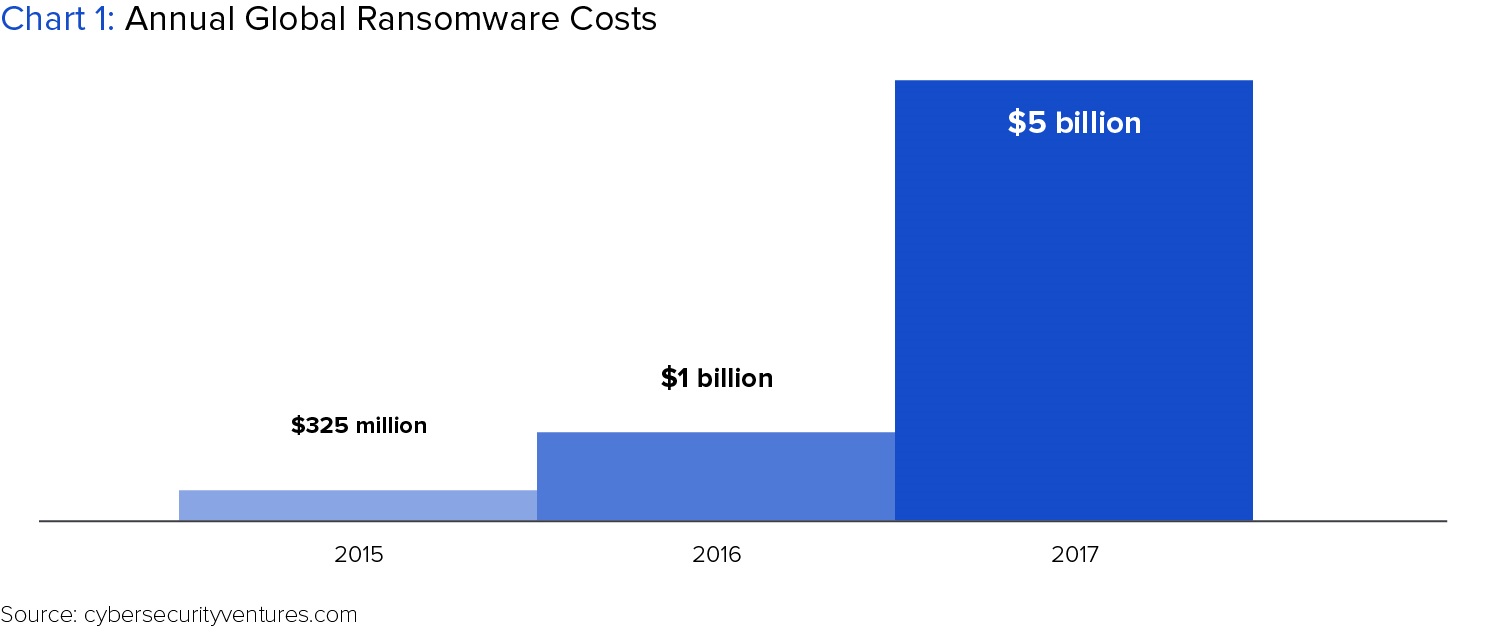
Higher education had the highest rate of ransomware attacks among all industries surveyed in a 2016 report published by BitSight (a cyber risk management company), and the second highest rate in BitSight’s 2017 report. Accordingly, universities are working around the clock to shore up their defenses against these steep potential losses. As Kim Milford, executive director of the Research and Education Networking Information Sharing and Analysis Center at Indiana University said in a 2016 piece written by the Center for Digital Education, universities are now “locked into an expensive arms race” as they explore new ways of both combatting current attacks and trying to stay one-step ahead of attacks yet to come. Regardless of whether cyberattacks are successful, Milford says, they represent a costly and ever-present issue that universities are forced to address.
Perhaps even more significant than potential financial losses, cyberattacks pose a grave threat to a university’s reputation and the safety of its students.
But the risks posed by cyberattacks extend beyond financial losses for the world of higher ed. Indeed, colleges and universities house a huge volume of sensitive data, from student social security numbers to valuable intellectual property, that, if stolen or compromised, could cause significant damage far beyond the walls of the academy. Perhaps even more significant than the aforementioned potential financial losses, cyberattacks pose a grave threat to a university’s reputation and the safety of its students.
Though threats are constantly evolving, colleges and universities must continue to invest in both the talent and infrastructure needed to meet cybersecurity challenges going forward. This article will further illuminate the importance of developing cybersecurity expertise for institutions of higher education and offer strategies for addressing these challenges. Beginning with an examination of why colleges and universities are uniquely vulnerable to cyberattacks, we will seek to understand the strategies attackers use to exploit these vulnerabilities and arrive at a set of recommendations designed to better equip colleges and universities to address cyber threats into the future.
Why Is Higher Education Vulnerable?
While virtually every major industry faces significant cybersecurity challenges, higher education is particularly vulnerable for a number of key reasons.
One has to do with academia’s unique culture, which prides itself on a degree of openness and transparency that most industries lack. As Fred Cate, director of the Indiana University Center for Applied Cybersecurity Research, articulated in a 2013 UniversityBusiness article, colleges and universities have historically focused efforts on making sure that “our faculty and our students and our public and our donors [can] connect pretty easily to us.” This has made college and university computer networks, the article says, “as open and inviting as their campuses.”
Another reason relates to history – specifically, how long colleges and universities have been online. Alex Heid, Chief Research Officer at SecurityScorecard (a third party risk management company) said in a 2016 EducationDIVE article that universities have always been prime targets for cyberattacks in large part because “Universities were one of the first places that had internet access, and with internet access you have people trying to see how far that can go.” By virtue of having had internet access for a relatively long time, colleges and universities have long been visible targets, and their weaknesses are therefore likely very well-known and understood by cyberattackers.
Cyberattackers use cutting edge technologies and methods to exploit university systems that are, in some cases, woefully outdated and outmatched.
Because colleges and universities were so early in adopting digital tools and interfaces (and as a result of financial and other practical concerns), many institutions of higher learning still rely on legacy systems that are particularly vulnerable to attacks. “A lot of the colleges use stuff that was written years ago,” Heid said in the aforementioned article. Put simply, cyberattackers use cutting edge technologies and methods to exploit university systems that are, in some cases, woefully outdated and outmatched.
More specifically, university IT systems are often characterized by a decentralized and, in Heid’s view, haphazard construction that attackers can easily exploit. In a 2017 blog post for data risk management and software firm Code42, Ashley Jarosch notes that while it may make sense from an operational perspective for individual departments to operate under their own IT structures (a university’s astrophysics department will likely, she writes, have different technological needs than a university’s literature department, for example), this sort of piecemeal setup creates clear information security vulnerabilities. “Across a dozen (or dozens of) departments, there’s a good chance at least one has some combination of outdated devices and unpatched OS, inadequate email filtering and AV, faulty data backup or insufficient user training and policy,” Jarosch writes.
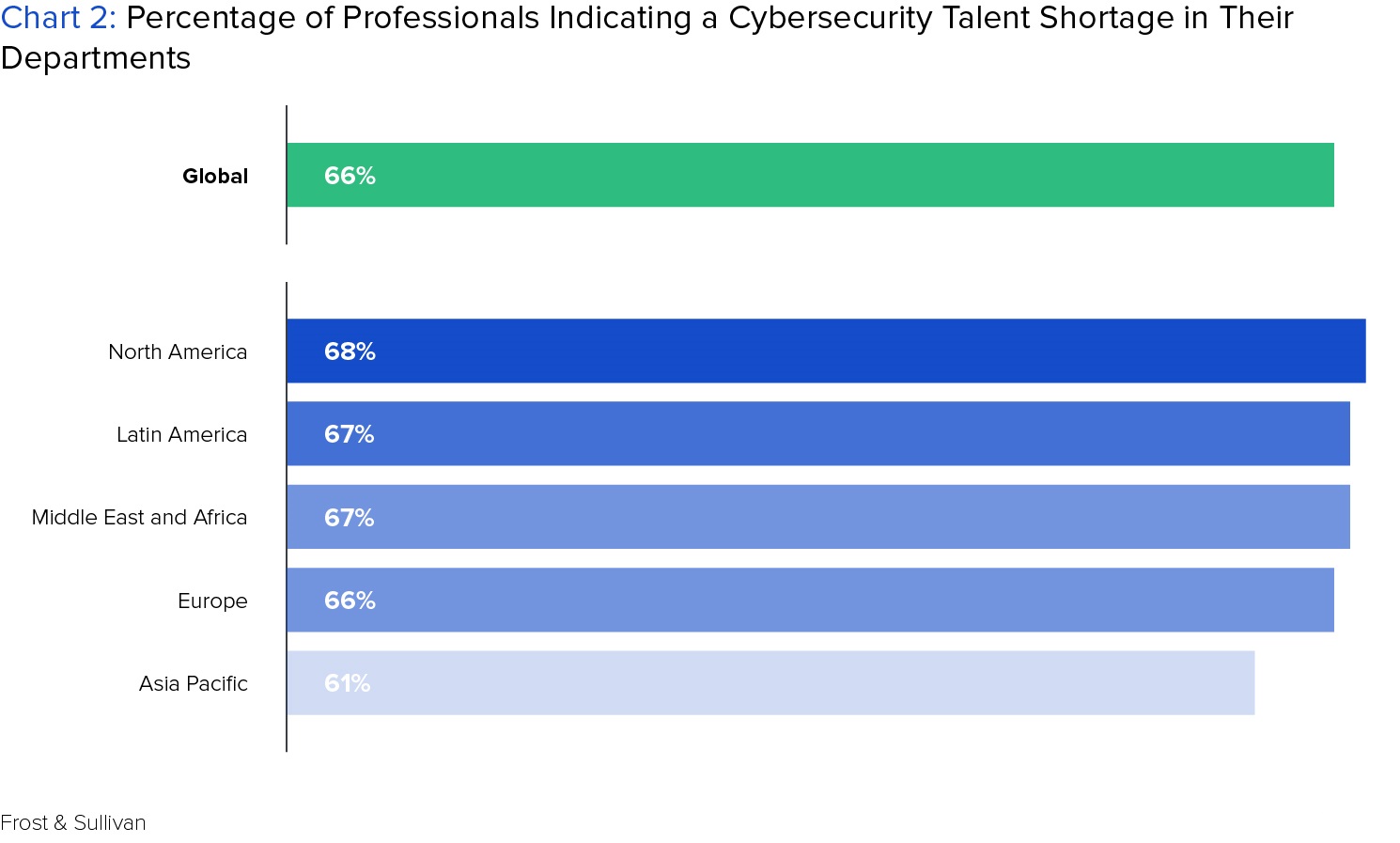
Though not an issue specific to higher education, the shortage in cybersecurity talent represents a significant obstacle that colleges and universities must overcome to address the issues mentioned above. A recent study conducted by consulting firm Frost & Sullivan projects that there will be 1.8 million unfilled cybersecurity jobs by 2020, and that this talent shortage exists on a global scale, with nearly 70 percent of professionals globally saying there are too few cybersecurity workers on staff. With demand for cybersecurity talent far outpacing supply, companies often pay top dollar for cybersecurity expertise. This likely puts colleges and universities at a serious disadvantage when attempting to lure such talent away from high paying private sector jobs at Alphabet, Facebook, and the like.
With an understanding of the reasons underlying higher education’s cybersecurity vulnerabilities, we can now explore the ways in which these vulnerabilities are exploited.
How Attackers Exploit Vulnerabilities
Nefarious actors employ a diverse range of tactics and tools when launching cyberattacks. Two of the most common such methods are outlined below. While this list is by no means exhaustive, nor unique to colleges and universities, it will provide a greater understanding of exactly how hackers aim to exploit gaps in cybersecurity and prove useful in considering how best to stop such attacks going forward.
SQL Injections: Described by some as “arguably the most severe problem web applications face,” SQL Injections (SQLi) are, in simple terms, attacks designed to bypass password protections through exploiting the databases that underlie certain applications. SQL (Standard Query Language) is a language that manages and communicates with databases. SQL Injections work through exploiting weaknesses in the code underlying input pages (such as username and password login pages, for example) and forcing a given database to return sensitive information. For example, when faced with a username and password login page, an attacker can enter (“inject”) a portion of SQL code into the password section. If the underlying database’s code is vulnerable, this SQL code could modify the underlying database and force the application that the database controls to allow the hacker access.
Colleges and universities have myriad password-protected online applications, from student grade reports to faculty employment information, that could theoretically be broken into using SQL Injections. One such attack on higher education came in February 2017, when a Russian hacker or hacker group used SQL Injections to steal data from dozens of U.S. colleges and universities, including Cornell University and New York University. As long as institutions of higher learning continue to have weaknesses written into their underlying databases, SQL Injections will likely remain common and all too easy for hackers to employ.
Phishing: As mentioned at the beginning of this article, phishing attacks are characterized by emails or web pages that are designed to fool users into entering sensitive data, such as passwords or credit card information. Princeton University’s Information Security Office provides a useful overview of how such attacks usually manifest:
“Typically, the phisher sends an email message to a large group of individuals whose addresses he has captured from address books and websites across the internet. The message, usually well-crafted and official-looking, may claim to be from a financial institution, a service provider, or any other organization known by the recipient…Often, the recipient is asked to provide the information by clicking a website link in the email. But while the link to the website may look legitimate, the link that is displayed is not necessarily the actual site you visit when you click on it.”
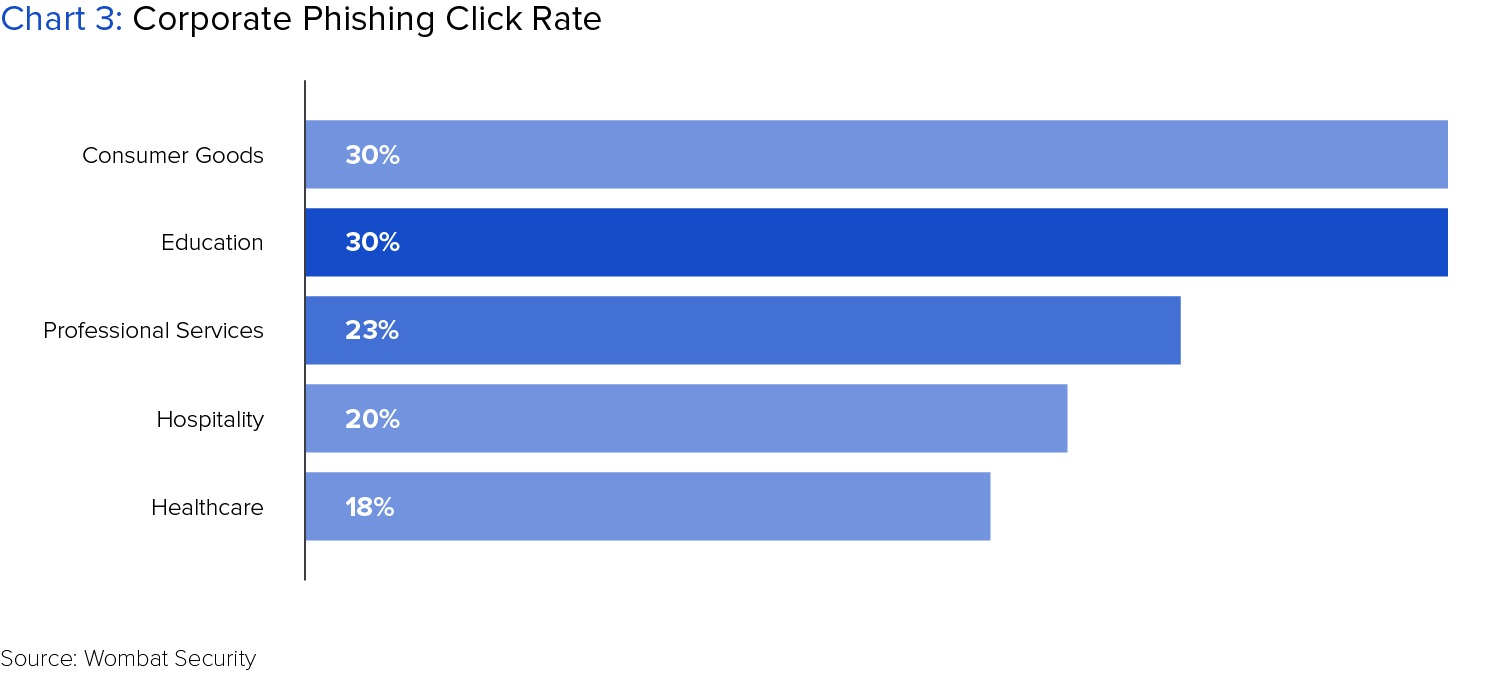
30 percent of users in the education industry have fallen for phishing scams posing as corporate communications, double the rate of the general population, in the last year.
While the tactics mentioned above have proven effective, we will see that they can be prevented.
How to Prevent Attacks: Better Code and Greater Vigilance
A number of strategies exist for combating the cyberattacks described above. Some involve strategies that higher education IT professionals must employ themselves, while others involve strategies that everyone in the higher education community, including end users, must implement:
Stopping SQLi attacks through Prepared Statements, Stored Procedures, and Input Validation
Much has been written about how to prevent SQL Injection attacks, and the consensus is that doing so may not actually be particularly difficult. The Open Web Application Security Project (OWASP) provides an overview of how to avoid SQLi attacks. OWASP cites three primary strategies for doing so:
Prepared Statements: Colleges and universities should construct their underlying databases with prepared statements. As OWASP says,“Prepared statements ensure that an attacker is not able to change the intent of a query, even if SQL commands are inserted by an attacker.” Essentially, prepared statements can render SQL commands posing as user input data (usernames and passwords) powerless.
Stored Procedures: According to OWASP, stored procedures can have the same effect as prepared statements, the primary difference being that “the SQL code for a stored procedure is defined and stored in the database itself, and then called from the application.” As OWASP and others have written, stored procedures may not always be appropriate for defense against SQLi attacks, but stand as a viable option for colleges and universities when written and implemented properly.
Input Validation: SQL injection attacks exploit applications and databases that do not cross-reference and validate inputted data. A logical step toward preventing these attacks is, therefore, to make sure that a database being constructed requires input validation. Microsoft also cites input validation as a key technique for avoiding SQLi attacks within its ASP.net web development model.
Preventing Phishing through Training and Heightened Suspicion
Unlike preventing SQLi attacks, which can be done through internal technical fixes, preventing phishing scams relies largely on end users – faculty, staff, and students. There are several steps colleges and universities should take to ensure that all end users stay vigilant:
Email filters: As an initial, simple step, colleges and universities should set up email filters that send suspicious non-university emails to a user’s spam folder. While this is far from a foolproof fix, it is an important first step that can prevent malicious emails from reaching their targets.
Training and Awareness Campaigns: Colleges and Universities should require end users to go through training that covers what phishing is and how to recognize it. There are companies dedicated to providing this service, and institutions of higher learning must be willing to invest the time and resources necessary to properly educate their faculties and staffs. As an article in Infosecurity Magazine points out, this training should be repeated on a relatively regular basis and should expose users to a diverse range of phishing attacks. Providing examples of real attacks and creating a repository for such attacks, as Princeton University has done with its “Phish Bowl” can also boost awareness.
“Educating our customers in terms of safe computing brings one of the biggest paybacks.”
Sasi Pillay, Vice President of Information Technology Services & Chief Information Officer at Washington State University, says that he and his team hold an annual cybersecurity awareness month and have sought to create a general “cyber-awareness culture” to combat phishing — the university’s number one cybersecurity issue. “Educating our customers in terms of safe computing brings one of the biggest paybacks,” Pillay says.
Though the strategies listed above are not comprehensive and may not prevent every attack, they represent relatively simple steps that can yield significant benefits in higher education’s fight against would-be cyber threats.
The Keys to a Secure Future
Understanding vulnerabilities, how common cyberattacks work, and how to prevent such attacks is fundamental to creating a more secure – and financially stable – future for higher education. Yet cyber threats are constantly evolving, and there is no guarantee that the threats faced today (and the strategies for mitigating them) will resemble those going forward.
For Sasi Pillay, the long-term solution to cyber security must include fundamental changes to how software is written and designed.
“My dream, long-term vision is to be able to do secure computing in a compromised environment,” Pillay says. “What we need to do is significantly change how we write software today. Software development needs to be fortified so people take security risks and exposures into account.”
Another key to meeting future cybersecurity challenges, mentioned briefly in this article, is employing a robust, steady team of experts in the field. This is, of course, easier said than done, as university budgets are tight and talent is scarce. Still, there are a number of ways around this issue, including hiring expert freelancers and those willing to work remotely.
Though the cybersecurity challenges facing higher education are great and the cost of solving them is steep, the potential financial and reputational risks that come with insufficient defense are likely even higher. Institutions across the higher education landscape may find that effective cybersecurity solutions can ultimately pay for themselves.








Add comment